According to phishing.org, “Phishing is a cybercrime in which a target or targets are contacted by email, telephone or text message by someone posing as a legitimate institution to lure individuals into providing sensitive data such as personally identifiable information, banking, and credit card details, and passwords. The information is then used to access important accounts and can result in identity theft and financial loss.”
Here are some recent statistics:
- Organizations experienced a 46% increase in successful phishing attacks in 2021 over 2020.
- 83% of organizations experienced a successful attack in 2021.
- 86% of organizations faced bulk phishing attacks where the same emails were sent to many people.
- Of those organizations successfully attacked:
- 54% experienced a breach of customer or client data
- 48% experienced credential or account compromise
- 24% reported reputational damage
- 11% paid a financial penalty/regulatory fine
Do We Have Your Attention Now?
Phishing is one of the most prevalent forms of cybercrime. But your organization can avoid being a victim with some basic know-how. Understanding how to recognize scams and deceptive links, properly handle suspicious emails, and prevent phishing emails through technology and training is key to avoiding becoming a statistic.
How to Recognize Phishing Email Scams
Phishing emails tend to look like they are from a company or person you know or trust. Even though scammers often change and update their tactics, some signs can clue you into the email’s intent.
The most common emails share a message with a sense of urgency. The point of the email aiming to have you click on a link to solve a purported problem or take advantage of a special deal. Examples include:
- Notification of a suspicious activity or log-in attempt
- Claim that there is a problem with an account or payment information
- Requirement to confirm personal information
- A fake invoice requesting payment
- Eligibility for a government refund
- Offer of a coupon or free item, or announcement of winning a gift card
To verify the validity of any suspicious email, you will need to take a closer look.
The Sender’s Domain Name
The most obvious way to identify a phishing email is to look at the sender’s email domain. This is the section of the email after the @. With the exception of some small organizations, all legitimate businesses will have their own email domain and company accounts. If the email address domain is not affiliated with the alleged sender, it is undoubtedly a scam. Similarly, if the first part of the email is nonsensical, that’s a scam alert.
Examples:
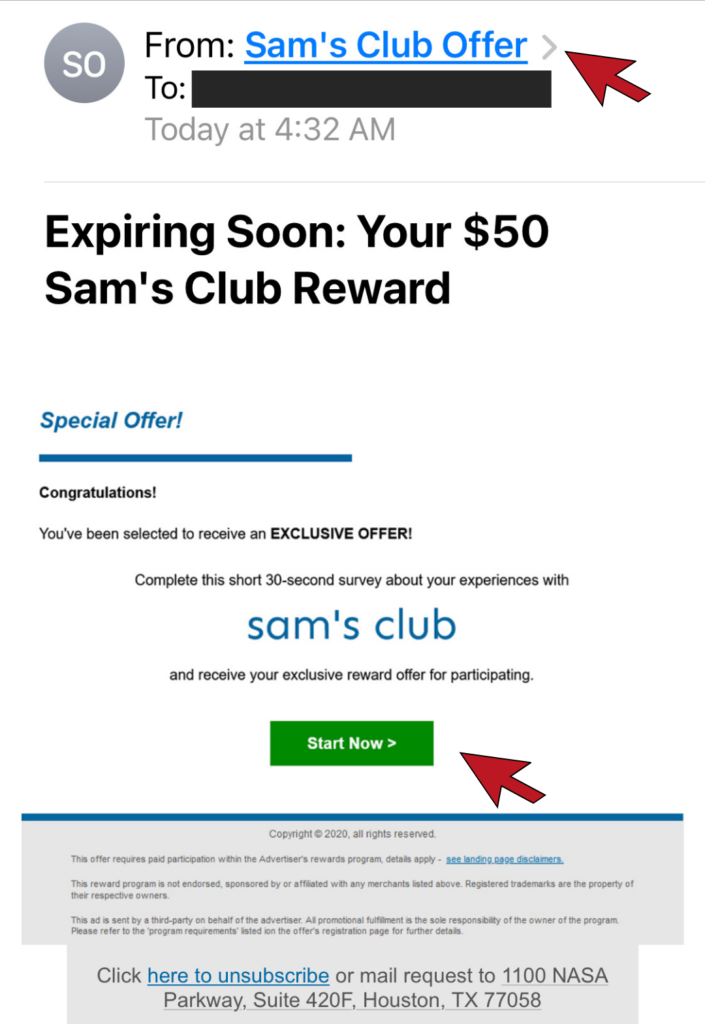
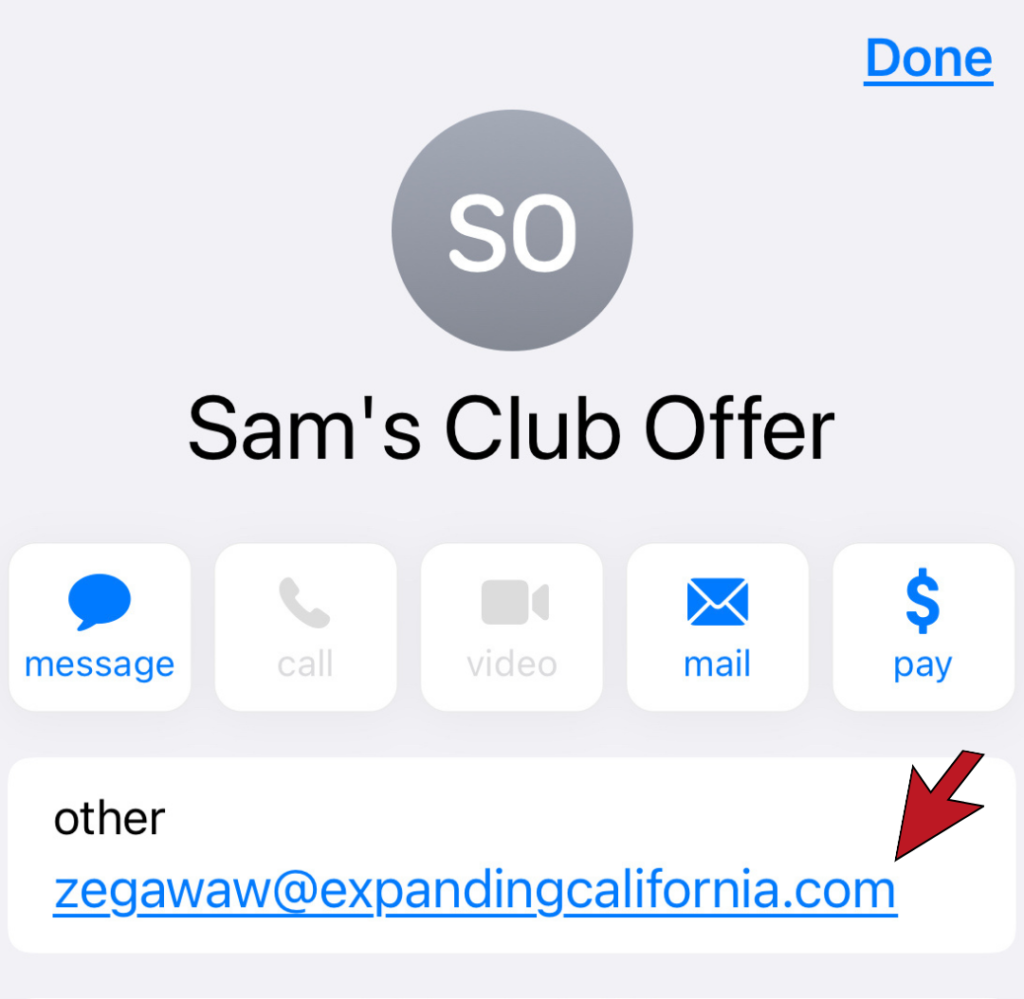
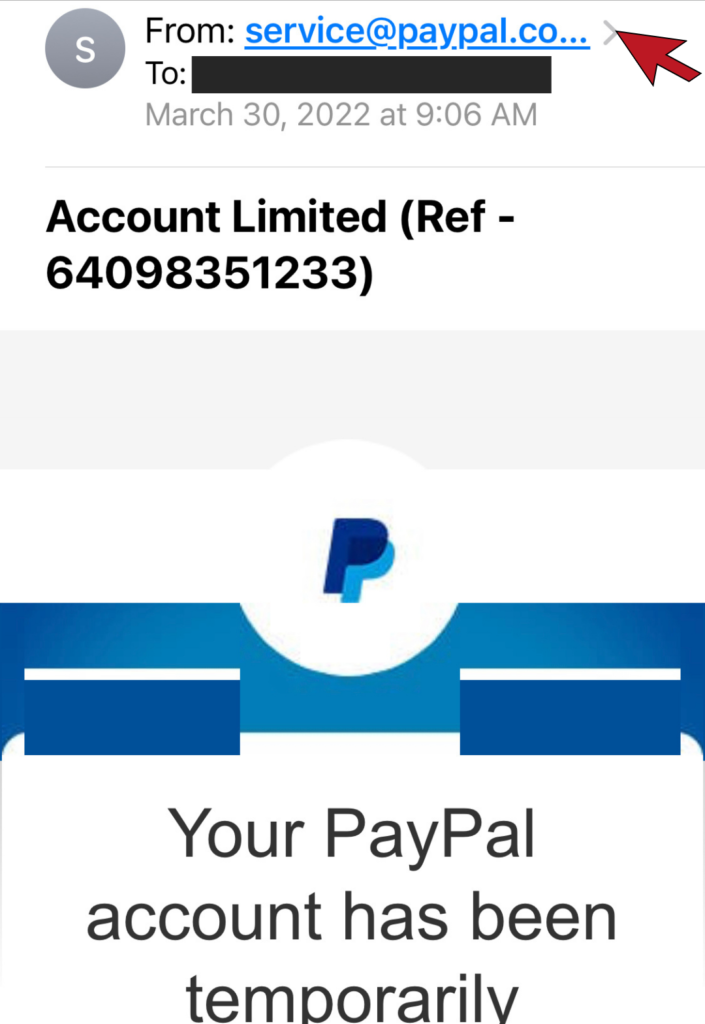
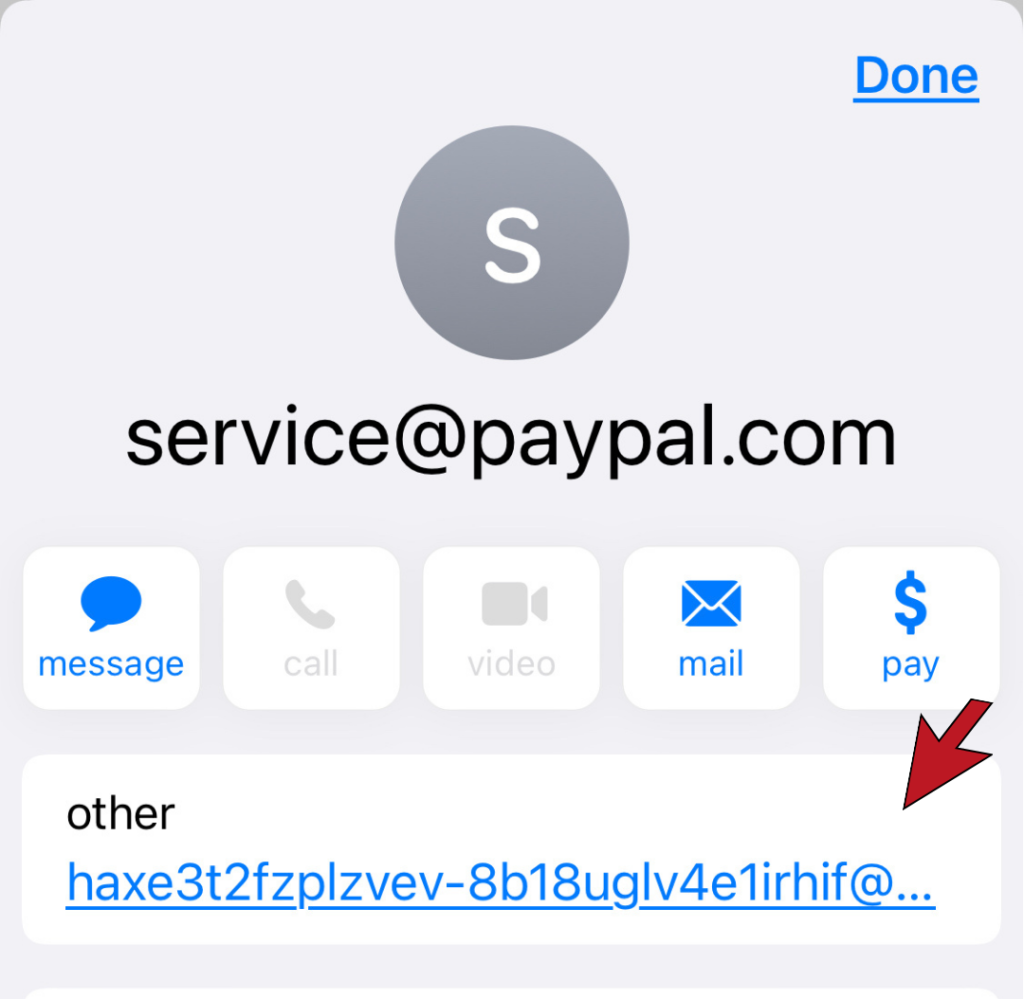
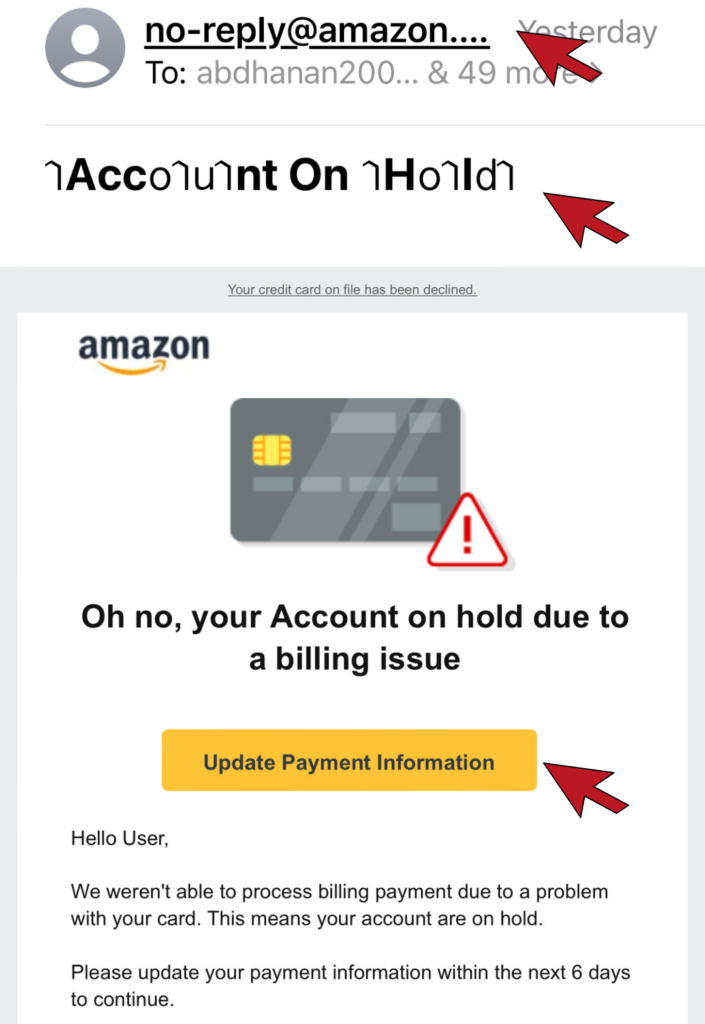
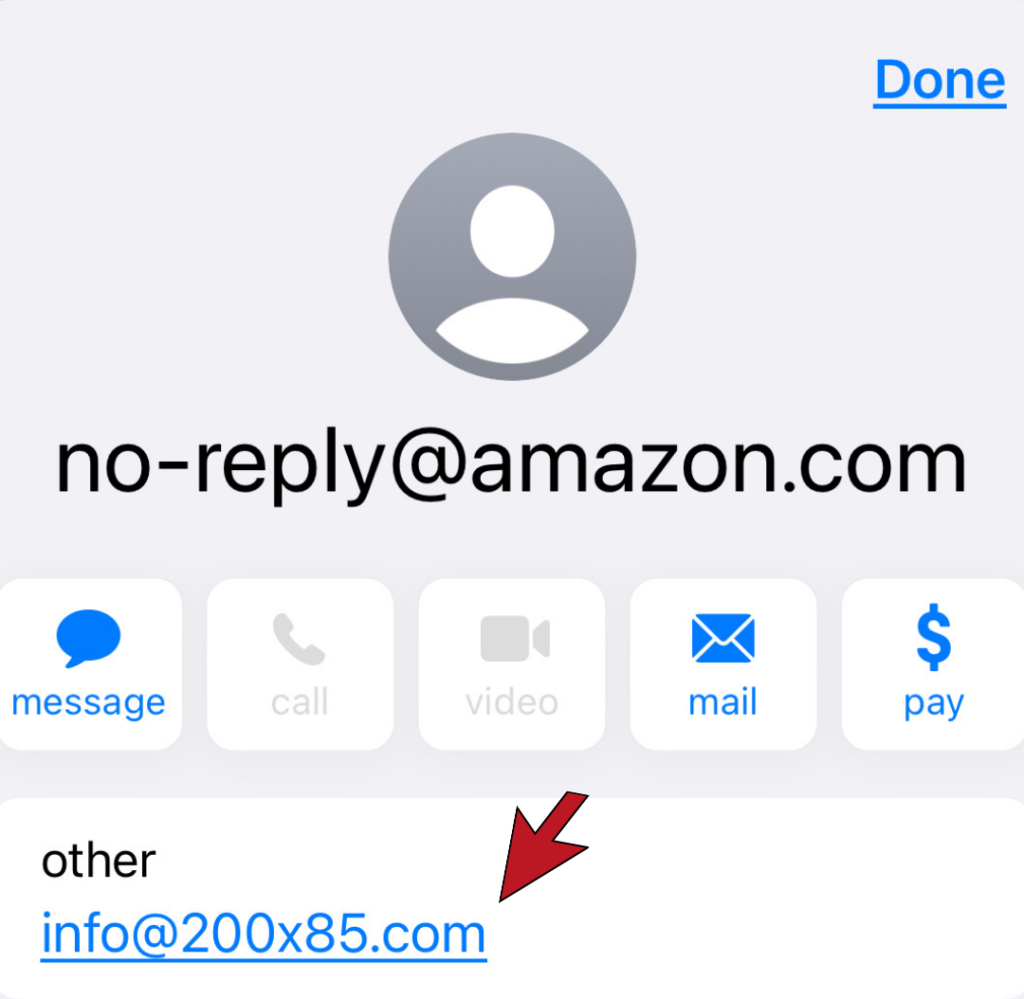
The Domain Name is Slightly Off
Savvy hackers have become wise to the fact people are beginning to check the sender’s domain. To get around this, hackers will create a false domain with a barely detectable misspelling of a valid company to try and fool you. For example, instead of services@microsoft.com, you might receive an email from services@microsft.com or services@rnicrosoft.com. It is necessary to inspect the domain name closely to avoid deception.
There are Spelling and Grammar Mistakes
So many phishing emails are poorly written because the hackers are from non-English speaking countries or from backgrounds where they have had limited opportunity to learn the language well. The hacker will often use a spellchecker or translation machine, which gives them the correct words but not necessarily in an appropriate context. Because of this, it is easier to spot the difference between a scam and a typo from a legitimate sender.
The Link is Suspicious
If the destination address of the hyperlink or call to action button does not match the context or sender of the email, you should be very suspicious. Hover over the link without clicking on it to see the destination URL. If the email is supposedly from Amazon, but the URL goes to www.greatescapesca.com, you have your answer. Do not click on the link!
There is a Suspicious Request from a Client or Vendor
Cybercriminals can get really sneaky when a person’s business email is compromised. They can read through the hacked account’s emails and determine what type of business is conducted with different organizations and contacts. They can then send correspondence to you from a validated email address containing the right domain name, logo, email signature, etc. It is practically impossible to discern whether or not it is a phishing scam by the methods mentioned above.
However, if you receive an email from a client or vendor with an unusual ask, such as requesting sensitive information, you may be the subject of an attack. In this case, the best course of action is to pick up the phone and call the email sender to validate the request. Be sure to pull the phone number from a previous email, though. The scammer may have updated the signature with a personal number.
The Danger of Phishing Email Links
When you unsuspectingly click on a phishing link, you are going to give sensitive information to someone who will exploit it, or you are opening up your computer or phone to malicious software. Either way, you or your company stand to lose a lot.
Although it is pretty obvious what to expect by sharing sensitive information with a hacker, there are myriad negative outcomes that can be experienced when malware such as viruses, worms, spyware, and ransomware is installed. The sad truth is that the average person will never detect it is happening. At least not until much damage has been done.
Malware will wreak havoc on your computer and network. Here are some of the impacts of a malicious software installation:
- Sensitive information stolen
- Computer slowed down as malware replicates itself and fills your hard drive
- Access to your files restricted
- Disruption of business on a larger scale as malware spreads throughout your network
- System crashing or freezing
- Pop-ups or unwanted programs disrupting workflow
- Spam sent from your email to coworkers or clients
What to Do With a Suspicious Email
Do not open it! The simple act of opening a phishing email may cause you to compromise your Personally Identifiable Information. Delete it immediately to avoid accidentally opening the message down the road. Never download any attachments in the email. Attachments in a phishing scam typically contain malware. Never click on the links which will direct you to fraudulent websites. Lastly, do not reply to the sender.
If you realize you have clicked on a phishing link, follow these steps:
- Disconnect your device from the internet immediately by either unplugging the internet cable or disconnecting Wi-Fi.
- Notify your IT department or Managed IT Services company immediately.
- Back up your files to avoid having your data destroyed or erased when you try to recover from the attack.
- Have your system scanned for malware. If this is outside of your level of technological expertise, hire a professional to do this.
- Change your usernames and passwords immediately. This applies to all online accounts, from email and online banking to social media and software apps.
How to Prevent Phishing Emails
As the saying goes, an ounce of prevention is worth a pound of cure. Your organization should invest in security software such as an anti-virus program. Software on both computer and mobile devices should be set to update automatically. Updates and patches provide critical protection against security threats. Protect your accounts by using multi-factor authentication, which will make it harder for your credentials to be hacked. Finally, back up your systems frequently to avoid data loss.
If it Looks Phishy…
Bottom line, if it looks phishy and smells phishy, it most likely is phishy! Although preventative measures are critical to protecting your operation, cybercriminals are always coming up with new ways to exploit the unwary. Training and educating your workforce will make a difference, and it’s not a bad idea to include it whenever you onboard a new employee.
FUSE3 offers cybersecurity measure implementation, hazard detection, susceptibility testing, security training, data loss prevention, ransomware remediation, and data recovery services. We powerfully shield your organization’s vital information with our total Computer Data Security solutions so that you can put your worries aside.
